Designate is a multi-tenant DNS-as-a-service that includes a REST API for domain and record management, a framework for integration with Neutron, and integration support for Bind9.
You would want to consider a DNSaaS for the following:
- A clean REST API for managing zones and records
- Automatic records generated (with OpenStack integration)
- Support for multiple authoritative name servers
- Hosting multiple projects/organizations
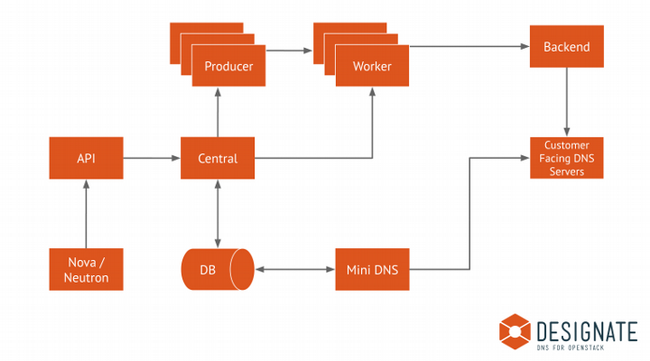
This article explains how to manually install and configure the latest release of Designate service on CentOS or Red Hat Enterprise Linux 7 (RHEL 7), but you can use the same configuration on other distributions.
Install Designate on OpenStack
I have Ansible roles for bind and Designate that demonstrate the setup in my GitHub repository.
This setup presumes bind service is external (even though you can install bind locally) on the OpenStack controller node.
- Install Designate's packages and bind (on OpenStack controller):
# yum install openstack-designate-* bind bind-utils -y - Create the Designate database and user:
MariaDB [(none)]> CREATE DATABASE designate CHARACTER SET utf8 COLLATE utf8_general_ci; MariaDB [(none)]> GRANT ALL PRIVILEGES ON designate.* TO \ 'designate'@'localhost' IDENTIFIED BY 'rhlab123'; MariaDB [(none)]> GRANT ALL PRIVILEGES ON designate.* TO 'designate'@'%' \ IDENTIFIED BY 'rhlab123';
Note: Bind packages must be installed on the controller side for Remote Name Daemon Control (RNDC) to function properly.
Configure bind (DNS server)
- Generate RNDC files:
rndc-confgen -a -k designate -c /etc/rndc.key -r /dev/urandom cat <<EOF> etcrndc.conf include "/etc/rndc.key"; options { default-key "designate"; default-server {{ DNS_SERVER_IP }}; default-port 953; }; EOF - Add the following into named.conf:
include "/etc/rndc.key"; controls { inet {{ DNS_SERVER_IP }} allow { localhost;{{ CONTROLLER_SERVER_IP }}; } keys { "designate"; }; };In the option section, add:
options { ... allow-new-zones yes; request-ixfr no; listen-on port 53 { any; }; recursion no; allow-query { 127.0.0.1; {{ CONTROLLER_SERVER_IP }}; }; };Add the right permissions:
chown named:named /etc/rndc.key chown named:named /etc/rndc.conf chmod 600 /etc/rndc.key chown -v root:named /etc/named.conf chmod g+w /var/named # systemctl restart named # setsebool named_write_master_zones 1 - Push rndc.key and rndc.conf into the OpenStack controller:
# scp -r /etc/rndc* {{ CONTROLLER_SERVER_IP }}:/etc/
Create OpenStack Designate service and endpoints
Enter:
# openstack user create --domain default --password-prompt designate
# openstack role add --project services --user designate admin
# openstack service create --name designate --description "DNS" dns
# openstack endpoint create --region RegionOne dns public http://{{ CONTROLLER_SERVER_IP }}:9001/
# openstack endpoint create --region RegionOne dns internal http://{{ CONTROLLER_SERVER_IP }}:9001/
# openstack endpoint create --region RegionOne dns admin http://{{ CONTROLLER_SERVER_IP }}:9001/Configure Designate service
- Edit /etc/designate/designate.conf:
- In the [service:api] section, configure auth_strategy:
[service:api] listen = 0.0.0.0:9001 auth_strategy = keystone api_base_uri = http://{{ CONTROLLER_SERVER_IP }}:9001/ enable_api_v2 = True enabled_extensions_v2 = quotas, reports - In the [keystone_authtoken] section, configure the following options:
[keystone_authtoken] auth_type = password username = designate password = rhlab123 project_name = service project_domain_name = Default user_domain_name = Default www_authenticate_uri = http://{{ CONTROLLER_SERVER_IP }}:5000/ auth_url = http://{{ CONTROLLER_SERVER_IP }}:5000/ - In the [service:worker] section, enable the worker model:
enabled = True notify = True - In the [storage:sqlalchemy] section, configure database access:
[storage:sqlalchemy] connection = mysql+pymysql://designate:rhlab123@{{ CONTROLLER_SERVER_IP }}/designate - Populate the Designate database:
# su -s /bin/sh -c "designate-manage database sync" designate
- In the [service:api] section, configure auth_strategy:
- Create Designate's pools.yaml file (has target and bind details):
- Edit /etc/designate/pools.yaml:
- name: default # The name is immutable. There will be no option to change the name after # creation and the only way will to change it will be to delete it # (and all zones associated with it) and recreate it. description: Default Pool attributes: {} # List out the NS records for zones hosted within this pool # This should be a record that is created outside of designate, that # points to the public IP of the controller node. ns_records: - hostname: {{Controller_FQDN}}. # Thisis mDNS priority: 1 # List out the nameservers for this pool. These are the actual BIND servers. # We use these to verify changes have propagated to all nameservers. nameservers: - host: {{ DNS_SERVER_IP }} port: 53 # List out the targets for this pool. For BIND there will be one # entry for each BIND server, as we have to run rndc command on each server targets: - type: bind9 description: BIND9 Server 1 # List out the designate-mdns servers from which BIND servers should # request zone transfers (AXFRs) from. # This should be the IP of the controller node. # If you have multiple controllers you can add multiple masters # by running designate-mdns on them, and adding them here. masters: - host: {{ CONTROLLER_SERVER_IP }} port: 5354 # BIND Configuration options options: host: {{ DNS_SERVER_IP }} port: 53 rndc_host: {{ DNS_SERVER_IP }} rndc_port: 953 rndc_key_file: /etc/rndc.key rndc_config_file: /etc/rndc.conf - Populate Designate's pools:
su -s /bin/sh -c "designate-manage pool update" designate
- Edit /etc/designate/pools.yaml:
- Start Designate central and API services:
systemctl enable --now designate-central designate-api - Verify Designate's services are up:
# openstack dns service list +--------------+--------+-------+--------------+ | service_name | status | stats | capabilities | +--------------+--------+-------+--------------+ | central | UP | - | - | | api | UP | - | - | | mdns | UP | - | - | | worker | UP | - | - | | producer | UP | - | - | +--------------+--------+-------+--------------+
Configure OpenStack Neutron with external DNS
- Configure iptables for Designate services:
# iptables -I INPUT -p tcp -m multiport --dports 9001 -m comment --comment "designate incoming" -j ACCEPT # iptables -I INPUT -p tcp -m multiport --dports 5354 -m comment --comment "Designate mdns incoming" -j ACCEPT # iptables -I INPUT -p tcp -m multiport --dports 53 -m comment --comment "bind incoming" -j ACCEPT # iptables -I INPUT -p udp -m multiport --dports 53 -m comment --comment "bind/powerdns incoming" -j ACCEPT # iptables -I INPUT -p tcp -m multiport --dports 953 -m comment --comment "rndc incoming - bind only" -j ACCEPT # service iptables save; service iptables restart # setsebool named_write_master_zones 1 - Edit the [default] section of /etc/neutron/neutron.conf:
external_dns_driver = designate - Add the [designate] section in /_etc/_neutron/neutron.conf:
[designate] url = http://{{ CONTROLLER_SERVER_IP }}:9001/v2 ## This end point of designate auth_type = password auth_url = http://{{ CONTROLLER_SERVER_IP }}:5000 username = designate password = rhlab123 project_name = services project_domain_name = Default user_domain_name = Default allow_reverse_dns_lookup = True ipv4_ptr_zone_prefix_size = 24 ipv6_ptr_zone_prefix_size = 116 - Edit dns_domain in neutron.conf:
dns_domain = rhlab.dev. # systemctl restart neutron-* - Add dns to the list of Modular Layer 2 (ML2) drivers in /etc/neutron/plugins/ml2/ml2_conf.ini:
extension_drivers=port_security,qos,dns - Add zone in Designate:
# openstack zone create –email=admin@rhlab.dev rhlab.dev.Add a new record in zone rhlab.dev:
# openstack recordset create --record '192.168.1.230' --type A rhlab.dev. Test
Designate should now be installed and configured.






1 Comment