If you're a Linux system administrator, you are probably familiar with using the Secure Shell (SSH) tool to securely connect to remote servers. You probably also know that SSH uses a public-private key pair to provide encryption. So, the first step in using SSH is to generate the key pair. You can also distribute your public key to remote servers so you can log into them without needing to type your password.
Seahorse, also referred to as Passwords and Keys, is a graphical tool for this purpose.
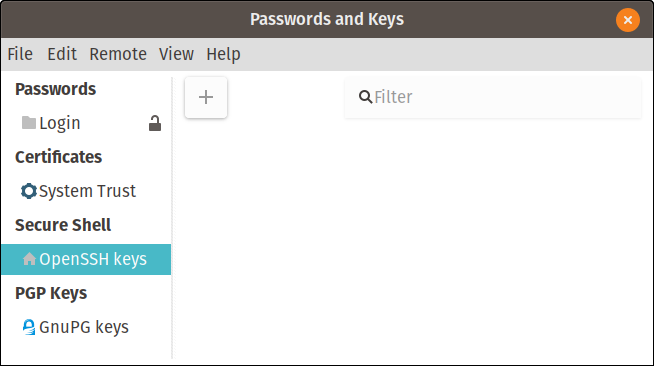
Seahorse's main screen
Its maintainer, the GNOME desktop project, calls it "Seahorse, a GNOME encryption interface," but you'll find it in your applications list as "Passwords and Keys." It can manage many different key types and logins, but I will focus on SSH. Just as with the command line version, its configuration will be stored in the usual .ssh subdirectory in your home directory.
Generating your key
You can generate a new key from the interface shown below. The command line for this is ssh-keygen. From the Seahorse GUI, click the plus (+) and select Secure Shell Key and Continue.
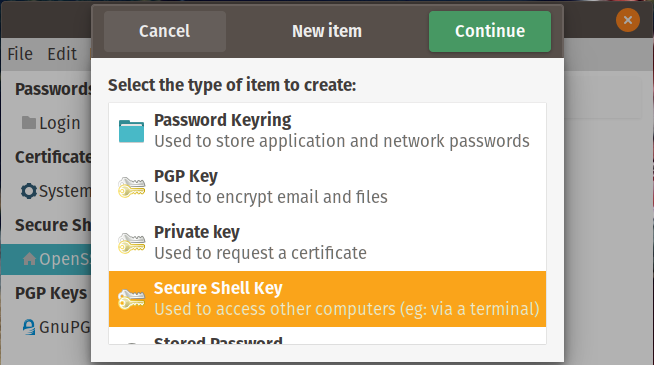
Select SSH Key to generate a key
The next screen provides a field to enter a description. You can also choose whether to go ahead and distribute this key to another system you want to connect to in the future, but for this example, click Just Create Key.
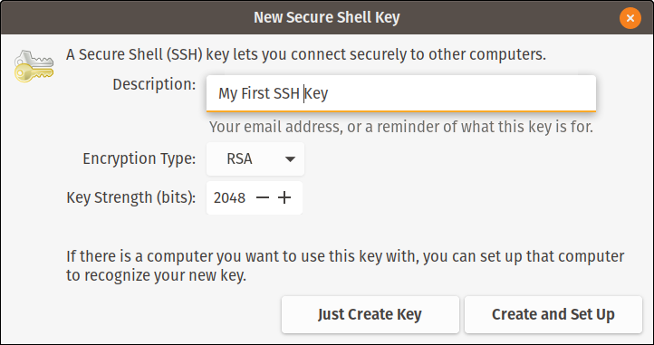
Creating a new SSH key
During the key-creation process, you'll be asked to enter a passphrase. I often leave this blank to avoid having to enter the passphrase each time I try to connect to another system; this interrupts the automation just like typing a password would. If you want to use my method, just click OK twice. Your new key is displayed in the interface.
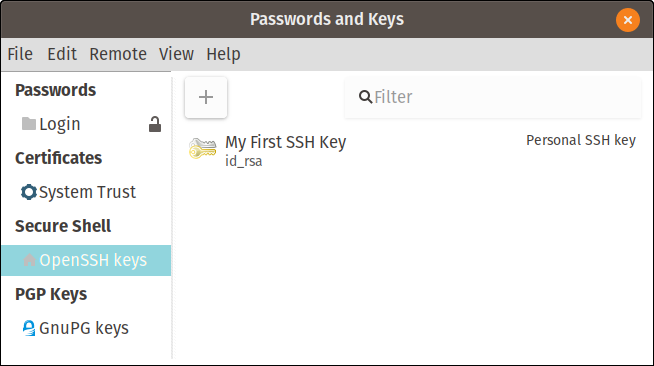
My first SSH key
You can also confirm the existence of your key pair by looking in your home directory's .ssh subdirectory.
alan@mainstation:~$ cd .ssh
alan@mainstation:~/.ssh$ ls -l
total 12
-rw------- 1 alan alan 1679 Apr 1 11:40 id_rsa
-rw-r--r-- 1 alan alan 398 Apr 1 11:40 id_rsa.pub
-rw-r--r-- 1 alan alan 222 Apr 1 10:54 known_hostsThere are two files that make up the SSH key pair. The file id_rsa is the private key. Notice that only you, the owner, will have read and write access to this file. It should not be shared with anyone. The file id_rsa.pub is the public key. It is safe to share since it is the file that is copied to a remote system when configuring key-based authentication. Let's look at that next.
Connect to a remote host
To use key-based authentication with a remote host, you need to copy your public key to that remote server. This is convenient because you don't need to type a password to log in. The command line for this is ssh-copy-id -i <identity file> <remote_host>. In the GUI, you can accomplish this by either clicking Remote from the menu bar or right-clicking on the SSH key. Select Configure Key for Secure Shell, and this window will appear:
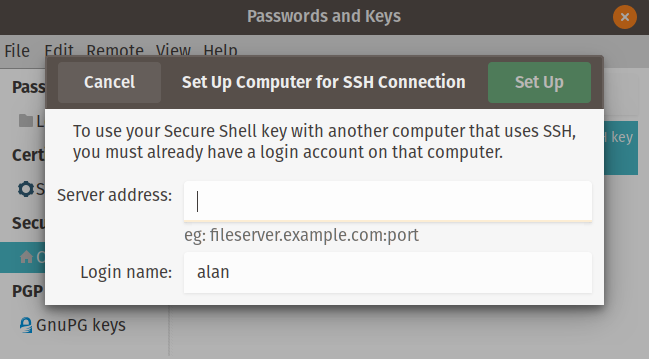
Configuring a remote server
Enter the hostname of the remote server and click Set Up. You'll be prompted for your remote server's login password, so enter it. There are no additional windows or prompts. You can now log into the remote server without needing to enter your password.
alan@mainstation:~$ ssh alan@workstation
Last login: Mon Apr 1 12:45:49 2019 from 192.168.2.6
alan@workstation:~$Get more help
Most of the time, we use SSH and its utilities at the command line. Download the SSH Cheat Sheet for a complete usage guide.








3 Comments