One of the main benefits of Linux systems is that they are known to be less prone to security vulnerabilities and exploits than other systems. Linux definitely gives users more flexibility and granular controls over its file systems' security permissions. This may imply that it's critical for Linux users to understand security permissions. That isn't necessarily true, but it's still wise for beginning users to understand the basics of Linux permissions.
View Linux security permissions
To start learning about Linux permissions, imagine we have a newly created directory called PermissionDemo. Run cd inside the directory and use the ls -l command to view the Linux security permissions. If you want to sort them by time modified, add the -t option.
ls -ltSince there are no files inside this new directory, this command returns nothing.
To learn more about the ls option, access its man page by entering man ls on the command line.
Now, let's create two files: cat.txt and dog.txt with empty content; this is easy to do using the touch command. Let's also create an empty directory called Pets with the mkdir command. We can use the ls -l command again to see the permissions for these new files.
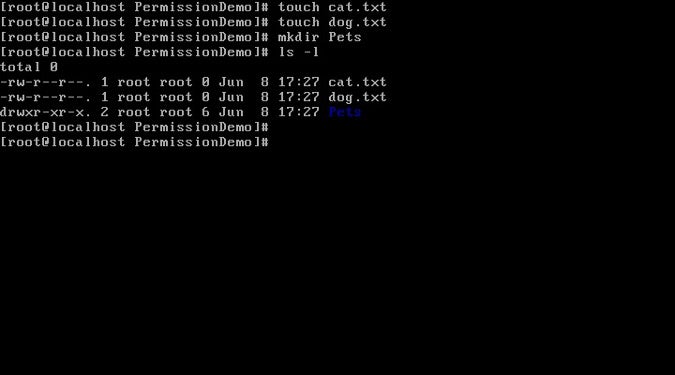
We need to pay attention to two sections of output from this command.
Who has permission?
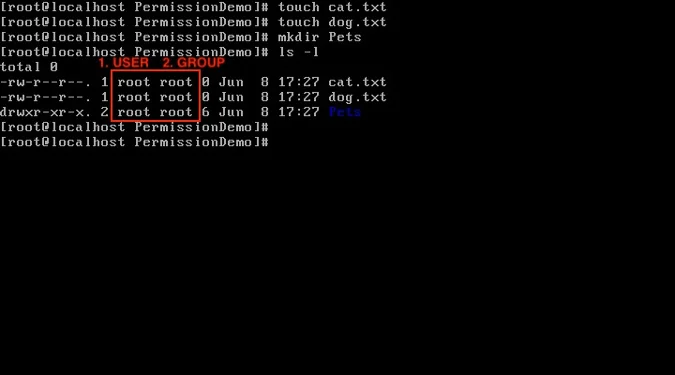
The first thing to examine indicates who has permission to access the file/directory. Note the section highlighted in the red box below. The first column refers to the user who has access, while the second column refers to the group that has access.
There are three main types of users: user, group; and other (essentially neither a user nor a group). There is one more: all, which means practically everyone.
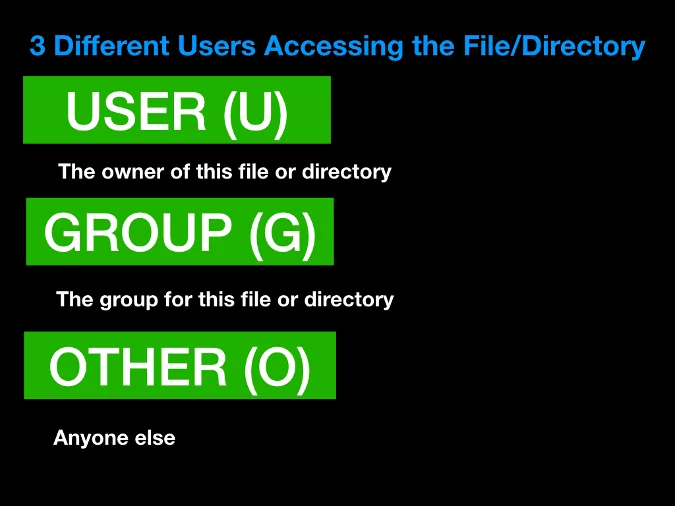
Because we are using root as the user, we can access any file or directory because root is the superuser. However, this is generally not the case, and you will probably be restricted to your username. A list of all users is stored in the /etc/passwd file.
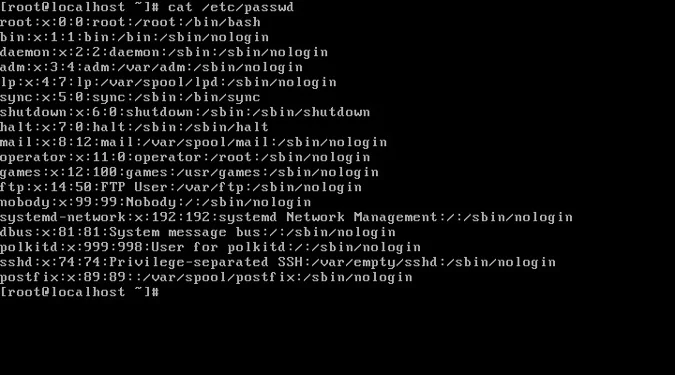
Groups are maintained in the /etc/group file.
What permissions do they have?
The other section of the output from ls -l that we need to pay attention to relates to enforcing permissions. Above, we confirmed that the owner and group permissions for the files dog.txt and cat.txt and the directory Pets we created belong to the root account. We can use that information about who owns what to enforce permissions for the different user ownership types, as highlighted in the red box below.
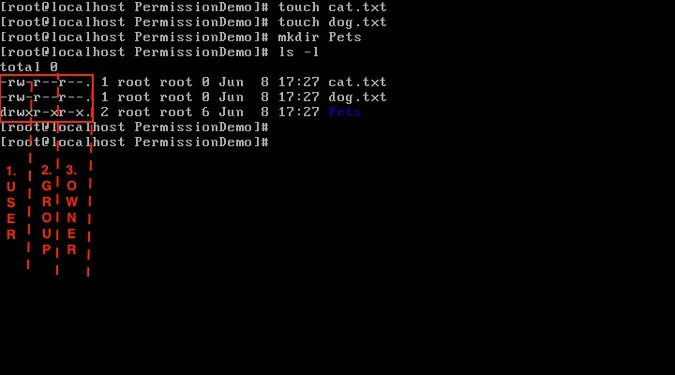
We can dissect each line into five bits of information. The first part indicates whether it is a file or a directory; files are labeled with a - (hyphen), and directories are labeled with d. The next three parts refer to permissions for user, group, and other, respectively. The last part is a flag for the access-control list (ACL), a list of permissions for an object.
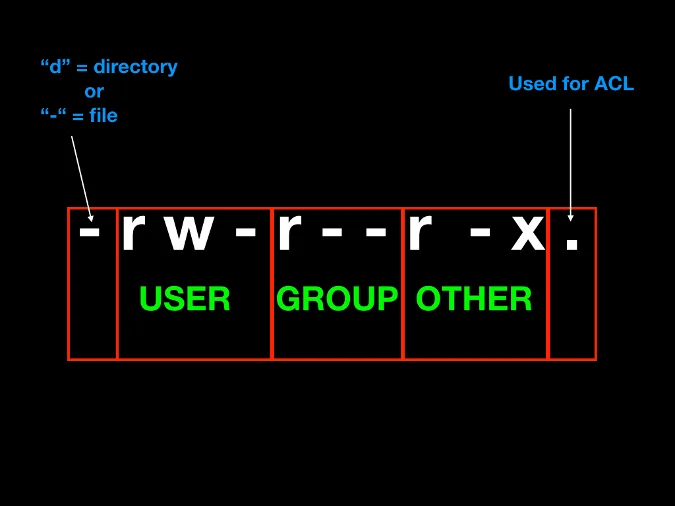
Linux permission levels can be identified with letters or numbers. There are three privilege types:
- read: r or 4
- write: w or 2
- executable: e or 1
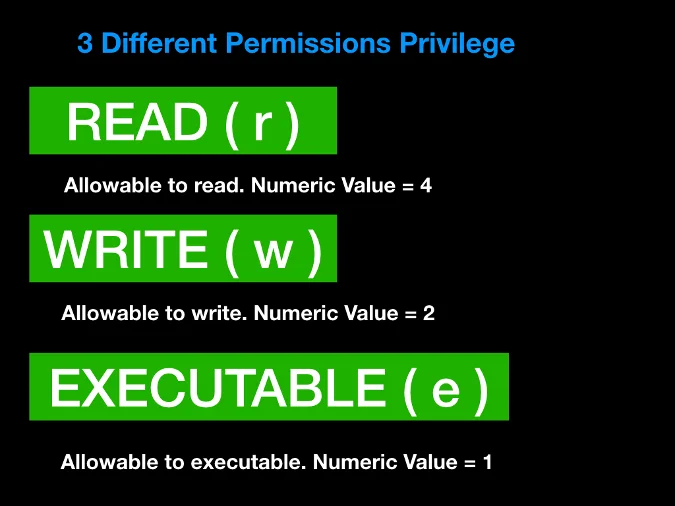
The presence of each letter symbol (r, w, or x) means that the permission exists, while - indicates it does not. In the example below, the file is readable and writeable by the owner, only readable if the user belongs to the group, and readable and executable by anyone else. Converted to numeric notation, this would be 645 (see the image below for an explanation of how this is calculated).
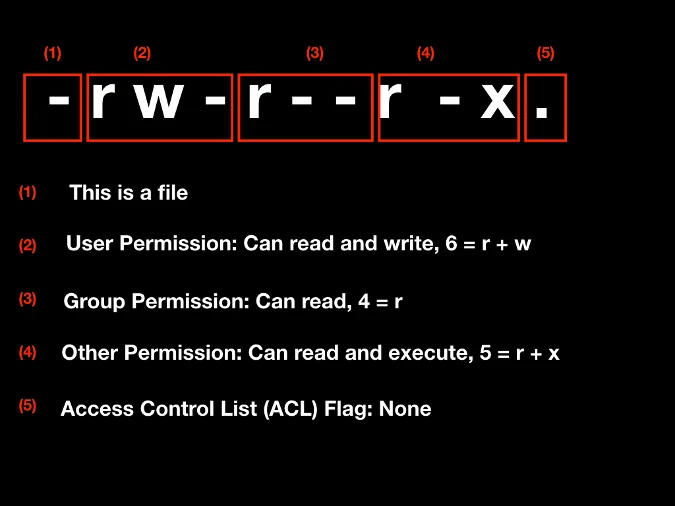
Here are a few more examples:

Test your knowledge by going through the following exercises.







5 Comments