First things first: What are proxy servers, and why use them?
Wikipedia provides the following description and diagram: A proxy server is a server (a computer system or an application) that acts as an intermediary for requests from clients seeking resources from other servers. A client connects to the proxy server, requesting some service, such as a file, connection, web page, or other resource available from a different server, and the proxy server evaluates the request as a way to simplify and control its complexity.
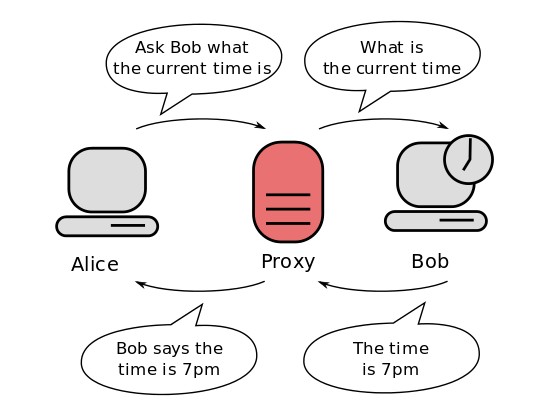
Proxy servers are useful in many contexts:
- In the office: to control internet traffic by blocking some websites or some keywords, to manage contact with external internet from a single point, or to optimize internet bandwidth usage by caching pages at proxy level.
- At home: to control family internet access to block dangerous websites for children.
- For personal use: to use an anonymous connection or to bypass network ISP blocks.
And those are just a few examples!
The Tor Project
From the Tor (anonymity network) Wikipedia page:
Tor is free and open source software for enabling anonymous communication. The name is derived from an acronym for the original software project name "The Onion Router." Tor directs internet traffic through a free, worldwide, volunteer overlay network consisting of more than 7000 relays to conceal a user's location and usage from anyone conducting network surveillance or traffic analysis. Using Tor makes it more difficult to trace Internet activity to the user; this includes "visits to websites, online posts, instant messages, and other communication forms." Tor's intended use is to protect the personal privacy of its users, as well as their freedom and ability to conduct confidential communication by keeping their Internet activities from being monitored.
Tor Project is the nonprofit association that currently develops software to facilitate the use of the Tor Network.
Do I need a Tor proxy or an alternative way to use the Tor network?
You can find a simple answer to this question with a few checks:
- If you can use a different browser within single computers, then you could evaluate Tor Browser. Tor Browser can be installed in your PC and allows you to browse the web with Tor network. A good installation guide comes from our friends at ProPrivacy.
- If you need a way to use the Tor network with your current browser or you need to connect a number of computers maintaining their current browsers, then you should opt for a Tor proxy. Read on for directions to install a Tor proxy in a cheap Raspberry Pi.
Step-by-step procedure
Hardware needed:
- a Raspberry Pi Zero W (or higher model) with its power supply (connected via WiFi)
- a micro SD card
In this guide, we are going to use default Raspbian Buster Lite as OS. Then we'll install Tor from Raspbian repository and apply a very simple configuration to use it as a Socks proxy.
I'll configure the Tor proxy to manage access for all clients on a 192.168.1.0/24 private network to internet. You will need to modify this network depending on your needs and networking configurations.
1. Install OS and Tor
Start from a fresh Raspbian Buster Lite installation. Make sure your OS is updated:
sudo apt-get update
sudo apt-get upgradeInstall Tor by using Raspbian repository:
sudo apt-get install torAt the end of the installation, you will have two services running as Tor: "tor.service" and "tor@default.service."
The first one is a dummy service, which appears to the user as active but in exited status. In fact, a simple check:
sudo systemctl status tor.servicewill give the following result:
● tor.service - Anonymizing overlay network for TCP (multi-instance-master)
Loaded: loaded (/lib/systemd/system/tor.service; enabled; vendor preset: enabled)
Active: active (exited) since Tue 2019-10-01 20:25:18 BST; 35s ago
Main PID: 5546 (code=exited, status=0/SUCCESS)
Memory: 0B
CGroup: /system.slice/tor.serviceThis is normal. The most reliable service to check if Tor is running is the second one. The command:
sudo systemctl status tor@default.serviceshould deliver a more familiar result:
● tor@default.service - Anonymizing overlay network for TCP
Loaded: loaded (/lib/systemd/system/tor@default.service; enabled-runtime; vendor preset: enabled)
Active: active (running) since Tue 2019-10-01 20:25:30 BST; 1min 36s ago
Main PID: 5552 (tor)
Memory: 23.5M
CGroup: /system.slice/system-tor.slice/tor@default.service
└─5552 /usr/bin/tor --defaults-torrc /usr/share/tor/tor-service-defaults-torrc -f /etc/tor/torrc --RunAsDaemon 02. Configure Tor
The Tor main configuration file is named torrc. Before editing, create a backup copy:
sudo cp /etc/tor/torrc /etc/tor/torrc.backupA very simple configuration will expose Tor Socks proxy service on Tor default port (9050) and will accept connections only from local LAN (192.168.1.0/24). It will run as daemon so that we won't need to call it each time we use it. Finally, it will store data in default directory (/var/lib/tor/).
Edit configuration file:
sudo nano /etc/tor/torrcincluding only the following lines (assuming that 192.168.1.100 is your Raspberry Pi IP address):
SocksPort 192.168.1.100:9050
SocksPolicy accept 192.168.1.0/24
RunAsDaemon 1
DataDirectory /var/lib/torClose and save the file, then restart Tor service:
sudo systemctl restart tor@default.service3. Configure your client to use a proxy server
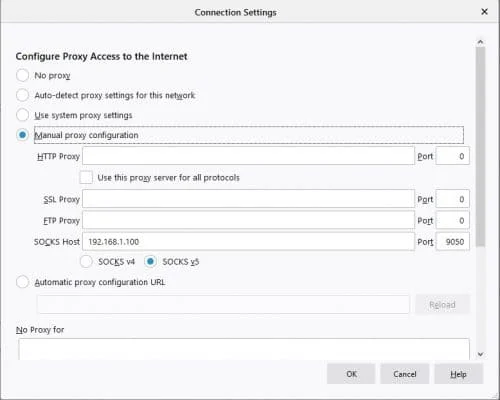
Now you need to configure your client to use Socks proxy server for internet connections. You have to check this, depending on your client browser. Mozilla Firefox can use Socks proxy and can be configured by selecting Options, Network Settings, then Settings. Select Manual Proxy Configuration, insert the Raspberry Pi IP address in the Socks Host field, insert 9050 in the related port and make sure SOCKS v5 flag is active. You should have a configuration like the following picture:
Close and then restart your browser. Now you are using your Tor network in your browser. You can verify it by browsing the URL https://check.torproject.org/?lang=en.
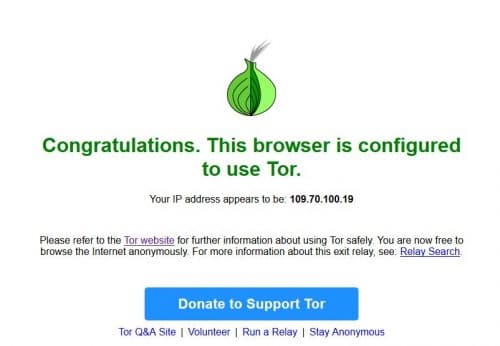
Enjoy!
This article was originally posted at peppe8o.com and has been published with the author's permission.








14 Comments